4.19. Firewall Configuration
Red Hat Enterprise Linux offers firewall protection for enhanced system security. A firewall exists between your computer and the network, and determines which resources on your computer remote users on the network can access. A properly configured firewall can greatly increase the security of your system.
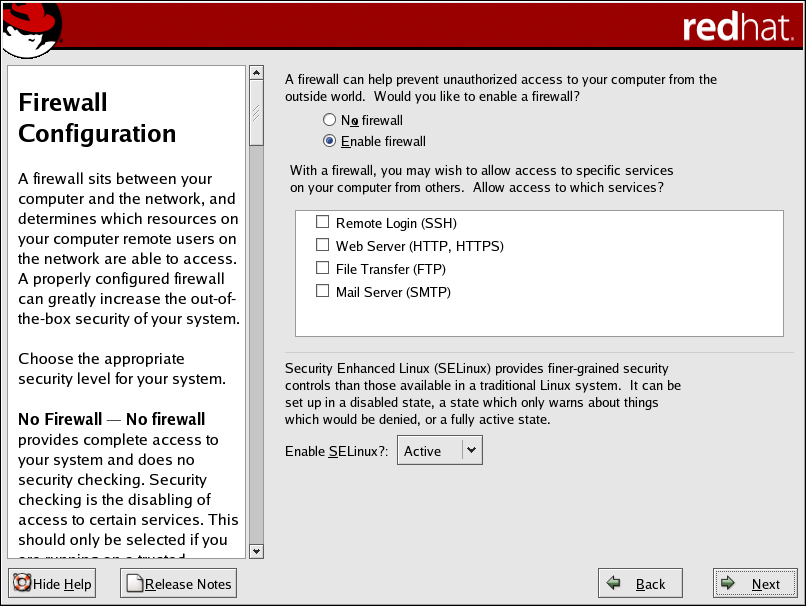
Next, you can decide whether to enable a firewall for your Red Hat Enterprise Linux system.
- No firewall
No firewall provides complete access to your system and does no security checking. Security checking is the disabling of access to certain services. This should only be selected if you are running on a trusted network (not the Internet) or plan to do more firewall configuration later.
- Enable firewall
If you choose Enable firewall, connections are not accepted by your system (other than the default settings) that are not explicitly defined by you. By default, only connections in response to outbound requests, such as DNS replies or DHCP requests, are allowed. If access to services running on this machine is needed, you can choose to allow specific services through the firewall.
If you are connecting your system to the Internet, this is the safest option to choose.
Next, select which services, if any, should be allowed to pass through the firewall.
Enabling these options allow the specified services to pass through the firewall. Note, these services may not be installed on the system by default. Make sure you choose to enable any options that you may need.
- Remote Login (SSH)
Secure Shell (SSH) is a suite of tools for logging in to and executing commands on a remote machine. If you plan to use SSH tools to access your machine through a firewall, enable this option. You need to have the openssh-server package installed in order to access your machine remotely, using SSH tools.
- Web Server (HTTP, HTTPS)
The HTTP and HTTPS protocols are used by Apache (and by other Web servers) to serve webpages. If you plan on making your Web server publicly available, enable this option. This option is not required for viewing pages locally or for developing webpages. You must install the httpd package if you want to serve webpages.
- File Transfer (FTP)
The FTP protocol is used to transfer files between machines on a network. If you plan on making your FTP server publicly available, enable this option. You must install the vsftpd package in order to publicly serve files.
- Mail Server (SMTP)
If you want to allow incoming mail delivery through your firewall, so that remote hosts can connect directly to your machine to deliver mail, enable this option. You do not need to enable this if you collect your mail from your Internet Service Provider's server using POP3 or IMAP, or if you use a tool such as fetchmail. Note that an improperly configured SMTP server can allow remote machines to use your server to send spam.

Note By default, the Sendmail mail transport agent (MTA) does not accept network connections from any host other than the local computer. To configure Sendmail as a server for other clients, you must edit /etc/mail/sendmail.mc and change the DAEMON_OPTIONS line to also listen on network devices (or comment out this option entirely using the dnl comment delimiter). You must then regenerate /etc/mail/sendmail.cf by running the following command (as root):
make -C /etc/mail
You must have the sendmail-cf package installed for this to work.
Additionally, you can now setup SELinux (Security Enhanced Linux) during your installation of Red Hat Enterprise Linux.
SELinux allows you to provide granular permissions for all subjects (users, programs, and processes) and objects (files and devices). You can safely grant an application only the permissions it needs to do its function.
The SELinux implementation in Red Hat Enterprise Linux is designed to improve the security of various server daemons while minimizing the impact on the day-to-day operations of your system.
Three states are available for you to choose from during the installation process:
Disable — Select Disable if you do not want SELinux security controls enabled on this system. The Disabled setting turns enforcing off and does not set up the machine for the use of a security policy.
Warn — Select Warn to be notified of any denials. The Warn state assigns labels to data and programs, and logs them, but does not enforce any policies. The Warn state is a good starting place for users who eventually want a fully active SELinux policy, but who first want to see what effects the policy would have on their general system operation. Note that users selecting the Warn state may notice some false positive and negative notifications.
Active — Select Active if you want SELinux to act in a fully active state. The Active state enforces all policies, such as denying access to unauthorized users for certain files and programs, for additional system protection. Choose this state only if you are sure that your system can still properly function with SELinux fully enabled.
For additional information about SELinux, refer to the following URLs:
 | Tip |
|---|---|
To change your security configuration after you have completed the installation, use the Security Level Configuration Tool. Type the system-config-securitylevel command in a shell prompt to launch the Security Level Configuration Tool. If you are not root, it prompts you for the root password to continue. |